Overview
Netskope One DSPM supports onboarding, connecting to, and scanning across your GCP Projects, either individual projects or those which participate within a GCP Organization. These actions require programmatic access to connect to & scan the Data Stores, including assigning specific IAM roles & API permissions.
Instructions
The specific steps to follow depend on whether your GCP Project is a member of an organization or stands alone as an individual project. These steps will include actions you need to perform within the GCP Console. Click the tab below which corresponds to the project setup in question:
GCP Organization
Create Google Service Account
Begin by configuring a service account which will be dedicated to the Netskope One DSPM application's use.
These steps only need to be performed once on any single member GCP Project.
Excerpt: GCP: Onboarding: Service Account
More information about GCP's BigQuery IAM roles is available here. Click this lin
More information about GCP's BigQuery IAM roles is available here.
- Click this link to log into your GCP IAM Console, which will navigate you to IAM & Admin > Service Accounts screen.
- Using the GCP project selector, navigate to the project for which you’d like to create the service account.
- Click the CREATE SERVICE ACCOUNT button (circled below).

- In the Service account details section, complete the following fields:
| Field | Value |
|---|---|
| Service account name | Any value; it is recommended to include "Netskope One DSPM" in the name, to make it easier to identify |
| Service account description | Any value |
- Click the CREATE AND CONTINUE button.
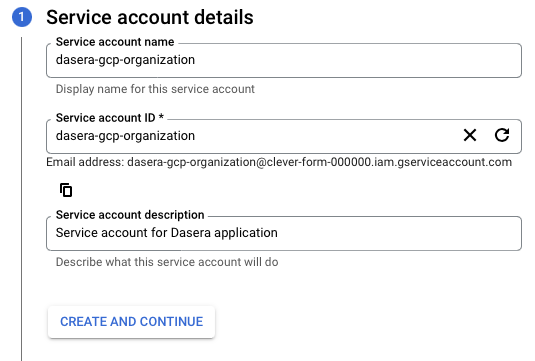
- Click the DONE button to complete creating the service account.
Add Custom IAM Roles
Netskope One DSPM Service Usage Role
Netskope One DSPM requires permission to specific Google APIs i.e. Cloud SQL Admin API, Cloud Data Catalog API, BigQuery API, and Cloud Resource Manager API to perform its scanning & discovery activities. A custom role needs to be created to automatically enable these APIs for all the projects under an organization during onboarding.
The following steps need to be performed to create this custom role
- Click this link to log into your GCP IAM Console, which will navigate you to IAM & Admin > Roles screen.
- Click the CREATE ROLE button.
- Complete the following fields:
| Field | Value |
|---|---|
| Title | Netskope One DSPM Service Usage |
| ID | CustomRoleXXX, where XXX could be any numeric |
- Click “Add Permissions” and type "Service Usage Admin" and select serviceusage.services.enable in the modal as shown below and click Add.
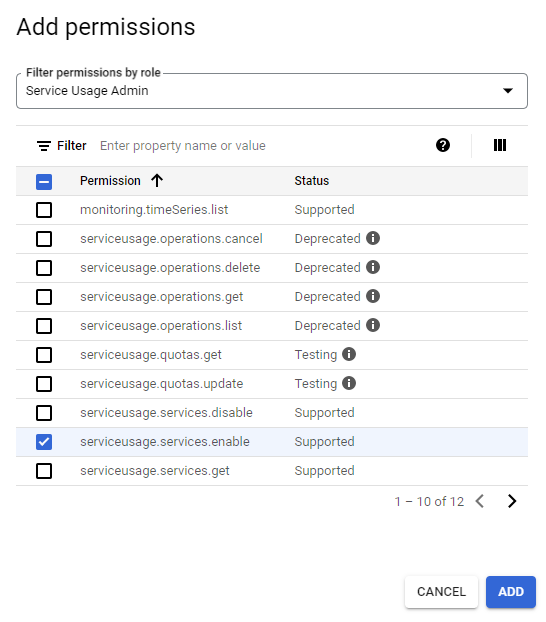
- To scan and classify data in Google Cloud Storage buckets, you must also add the following permissions:
- Filter permission list by Storage Admin role.
- Select the permissions shown in the image below.
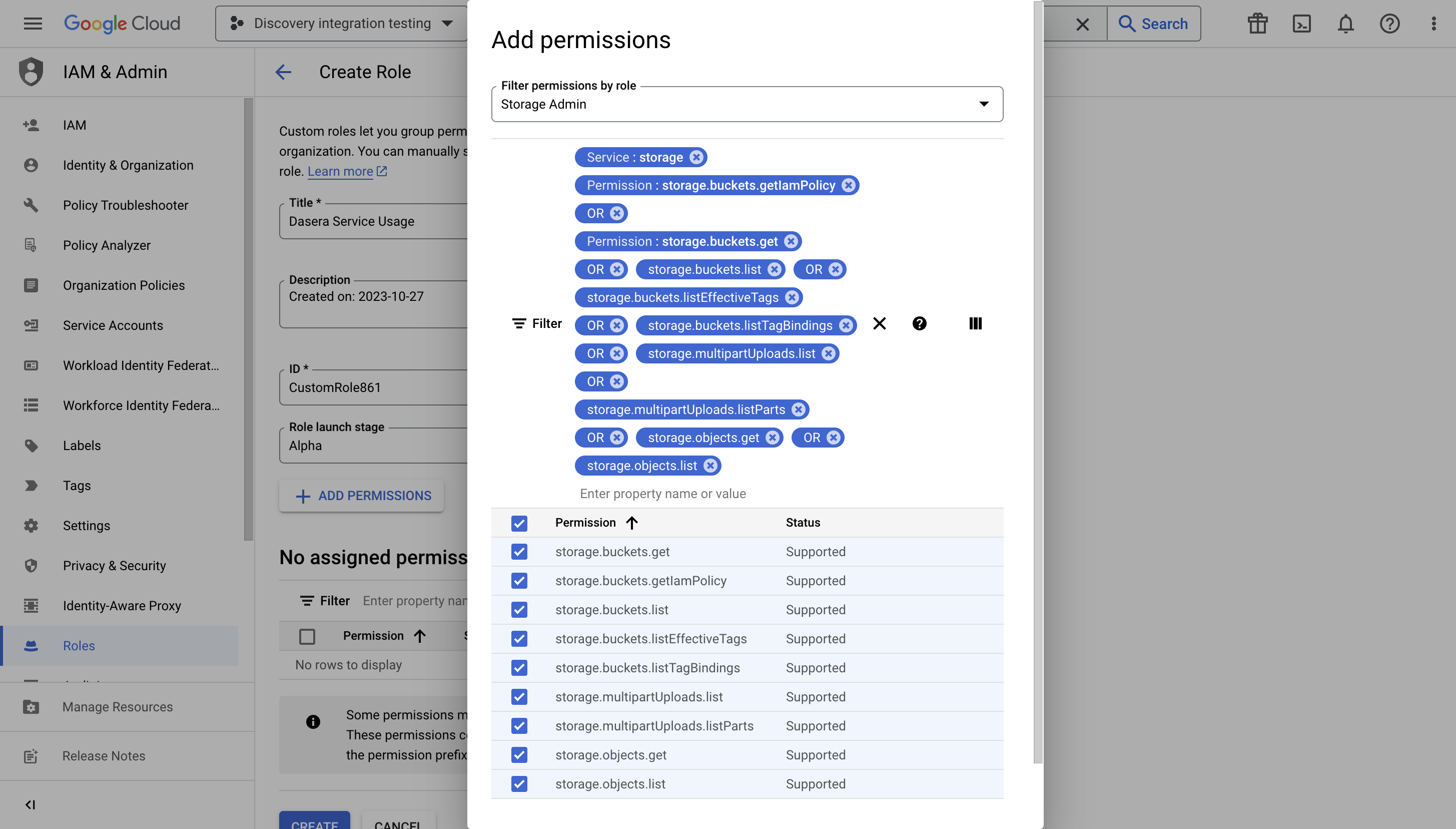
storage.buckets.get
storage.buckets.getIamPolicy
storage.buckets.list
storage.buckets.listEffectiveTags
storage.buckets.listTagBindings
storage.multipartUploads.list
storage.multipartUploads.listParts
storage.objects.get
storage.objects.list- Add permissions for persistent disk discovery
.png)
compute.disks.list
compute.instances.get
compute.instances.list- Click the CREATE button to complete.
Netskope One DSPM BigQuery Connection User Role
Netskope One DSPM requires a specific Bigquery custom role to be defined and applied to the service account for a seamless connection to the Bigquery data stores. Repeat the steps as above in the IAM & Admin > Roles screen to create the role.
| Field | Value |
|---|---|
| Title | Netskope One DSPM BigQuery Connection User |
| ID | CustomRoleXXX, where XXX could be any numeric |
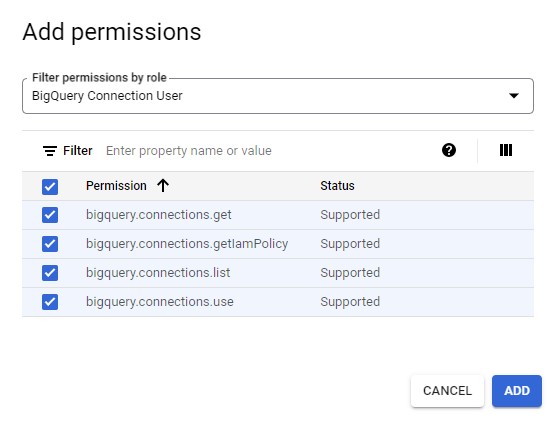
Click “Add Permissions” and type "BigQuery Connection User" and select all the permissions in the modal as shown below and click Add followed by CREATE button to complete.
Note that the BigQuery API must be enabled for each GCP Project for which you'll connect a BigQuery data store:
- Visit the specific API page
- Click ENABLE
- Once enabled, you will see the following:
Netskope One DSPM Unmanaged Discovery Role
Netskope One DSPM requires a specific custom role to be defined and applied to the service account for automatically discovering unmanaged data stores such as MySQL, PostgreSQL, MariaDB, Oracle and SQL Server, within GCP Persistent Disks. Repeat the steps as above in the IAM & Admin > Roles screen to create the role.
| Field | Value |
|---|---|
| Title | Netskope One DSPM Unmanaged Discovery Role |
| ID | CustomRoleXXX, where XXX could be any numeric |
Click “Add Permissions” and type "Netskope One DSPM Unmanaged Discovery Role" and select all the permissions listed below in the modal and click Add followed by CREATE button to complete.
compute.disks.create
compute.disks.createTagBinding
compute.disks.delete
compute.disks.get
compute.disks.list
compute.disks.listTagBindings
compute.disks.setLabels
compute.disks.update
compute.disks.use
compute.disks.useReadOnly
compute.images.useReadOnly
compute.instances.attachDisk
compute.instances.create
compute.instances.createTagBinding
compute.instances.delete
compute.instances.get
compute.instances.list
compute.instances.listTagBindings
compute.instances.setLabels
compute.instances.setMetadata
compute.subnetworks.use
compute.subnetworks.useExternalIp
compute.zoneOperations.get
resourcemanager.resourceTagBindings.create
resourcemanager.tagKeys.create
resourcemanager.tagKeys.get
resourcemanager.tagKeys.list
resourcemanager.tagValueBindings.create
resourcemanager.tagValues.create
resourcemanager.tagValues.get
resourcemanager.tagValues.listNote that the Compute Engine API must be enabled for each GCP Project for which you want to discover unmanaged data stores in GCP Persistent Disks.
Enabling this feature will result in additional costs. The total expense will vary based on the number of disks that require scanning, the duration of the scans, and the volume of data involved. These factors will determine how long the extra resources needed for scanning the disks remain active.
Elevate Service Account to Organization Principal
- Using the GCP project selector, navigate to your organization.
- Within the GCP IAM Console, click the GRANT ACCESS button.
- In the Add principals section, search for & add the service account you created above.
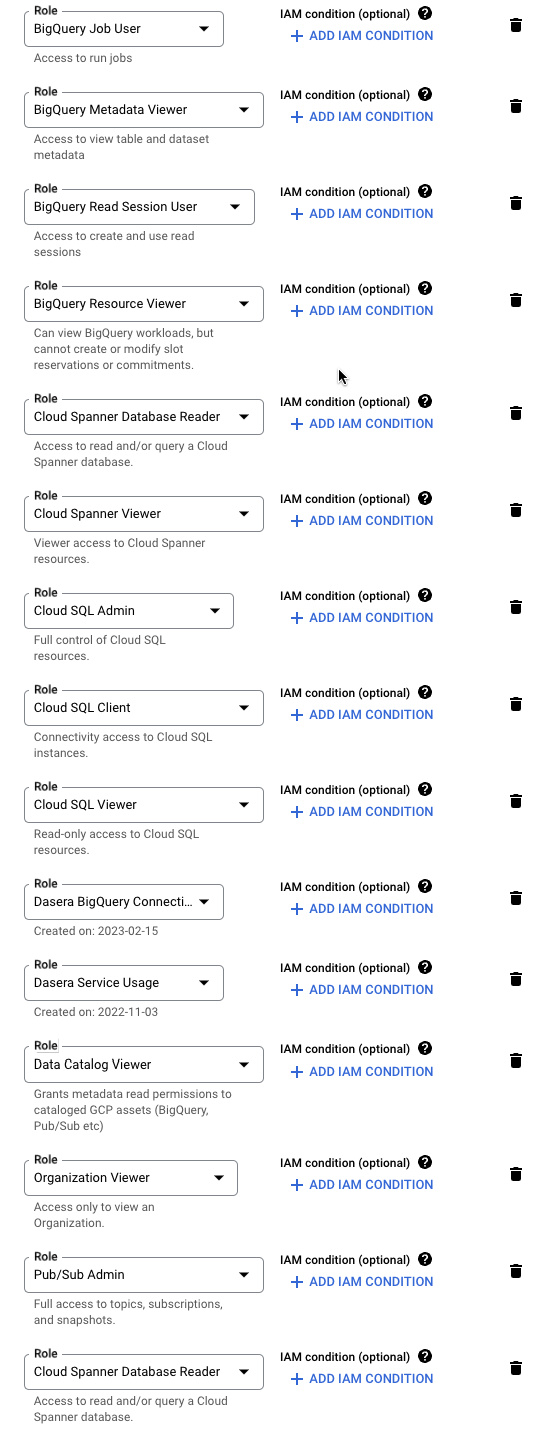
- In the Assign roles section, configure the service account's organization access by assigning the following GCP IAM roles:
- Netskope One DSPM Service Usage (as created in Add Custom IAM Role section)
- Netskope One DSPM BigQuery Connection User (as created in Add Custom IAM Role section)
- Netskope One DSPM Unmanaged Discovery Role (as created in Add Custom IAM Role section)
- Cloud Spanner Viewer
- Cloud Spanner Database Reader
- Cloud SQL Admin (must be included to use Snapshot Scan with Cloud SQL data stores)
- Cloud SQL Client
- Cloud SQL Viewer
- BigQuery Data Viewer
- BigQuery Job User
- BigQuery Metadata Viewer
- BigQuery Read Session User
- BigQuery Resource Viewer
- Data Catalog Viewer
- Organization Viewer
- Pub/Sub Admin (must be included to send notifications via Google Pub/Sub)
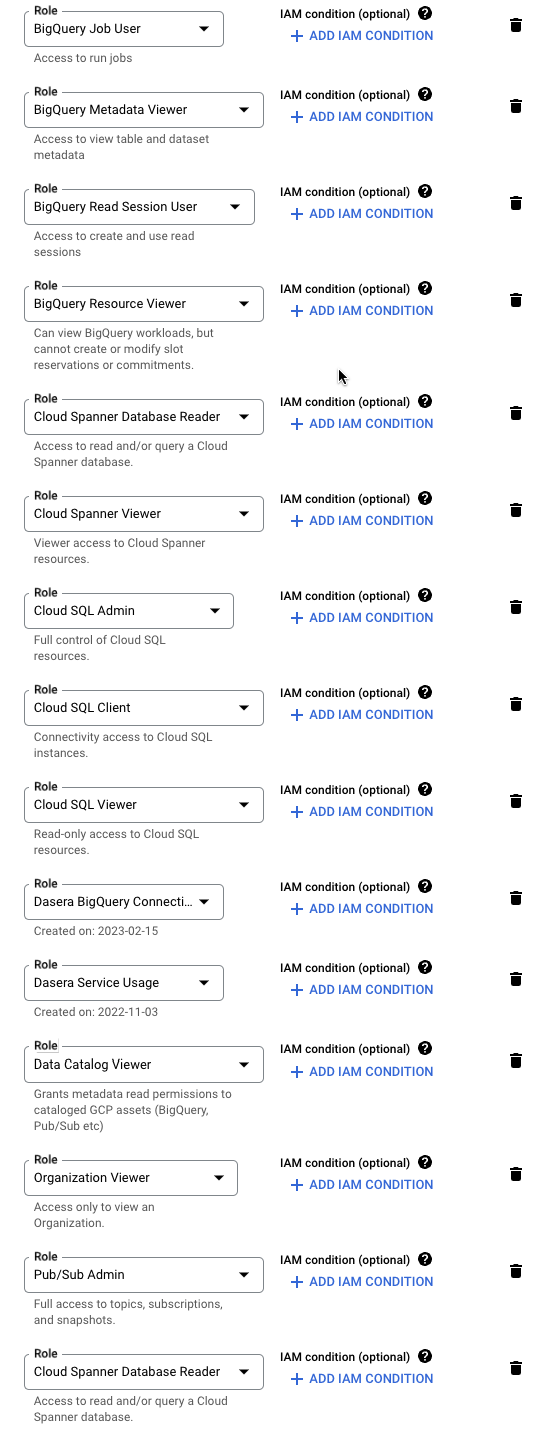
Click the SAVE button to complete the grant.
Generate Google Service Key
Excerpt: GCP: Onboarding: Service Key
Once the Netskope One DSPM-specific service account has been created, you can generate and download a service key, which the Netskope One DSPM platform will use for connecting with your GCP infrastructure.
- Click this link to log into your GCP IAM Console, which will navigate you to IAM & Admin.
- Within the GCP IAM Console, click on the project for which you created the above service account
- Select the service account's details by either:
- Clicking its Email hyperlink; or
- Under the Actions column, click the three-dot icon to display the sub-menu, then select Manage Details.
- Click on the KEYS tab.
- Click the ADD KEYS button.
- In the displayed dropdown list, select “Create new key”.
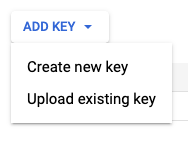
- On the next screen, ensure that "Key type" equals "JSON".
- Click the CREATE button to download the JSON Key File to your local machine. This file will be used in the Create a Netskope One DSPM Infrastructure Connection section below

Create Netskope One DSPM Infrastructure Connection
Once a GCP Organization is connected, every member project will be automatically onboarded within the Netskope One DSPM application, including members added in the future.
Excerpt: GCP: Onboarding: Infrastructure Connection 1
At this point, your configuration of GCP infrastructure is complete, and it can now be onboarded to the Netskope One DSPM application.
- Log into your Netskope One DSPM instance.
- Navigate to Administration > Infrastructure Connections.
- Select the GCP tab.
- Click the Add Infrastructure button.
- The Add Infrastructure modal is displayed.
- In the JSON Key File field, upload the JSON key you created above.
- Enter the following additional values:
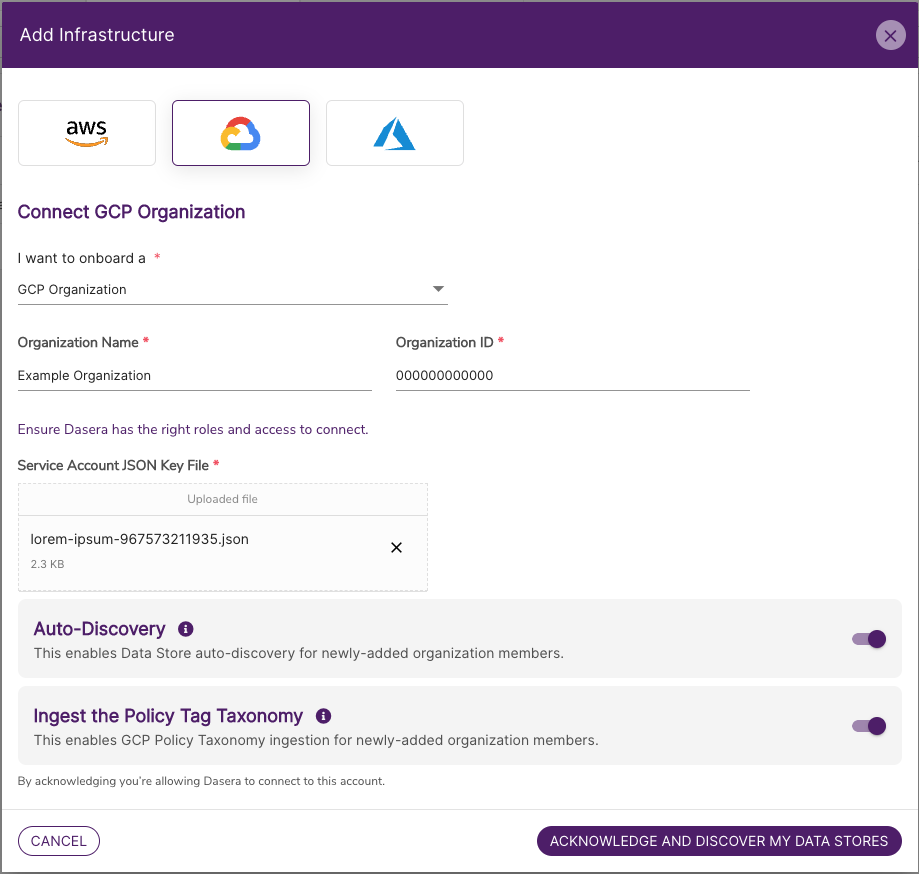
| Field | Value |
|---|---|
| I want to onboard a | GCP Organization |
| Organization Name | Any value (this is used to identify your Infrastructure Connection within the Netskope One DSPM UI). |
| Organization ID | Your GCP Organization ID, which can be found within the GCP Console under the IAM & Admin > Manage Resources screen. |
- Confirm your desired organization defaults, which set the corresponding values for member projects when they are onboarded (you can change your choices at anytime):
Excerpt: GCP: Onboarding: Infrastructure Connection 2
| Setting | Details When Enabled |
|---|---|
| Auto-Discovery | Netskope One DSPM will discover Data Stores within a GCP Project. To learn more, please visit our Data Store Inventory article. |
| Ingest the Policy Tag Taxonomy | Any GCP Policy Taxonomies associated with a GCP Project will be imported. To learn more, please visit our Data Tags article. |
- Click the Acknowledge button.
At this point, we recommend that you permanently delete your local copy of the JSON Key File, to prevent any unauthorized use.
Netskope One DSPM will next verify the connection, onboard your project(s), and kick off the initial discovery of Data Stores. Once you've completed onboarding GCP Projects, the GCP Infrastructure Connections screen will resemble the following. Blank Organization Name values indicate individual GCP projects outside of any organization.
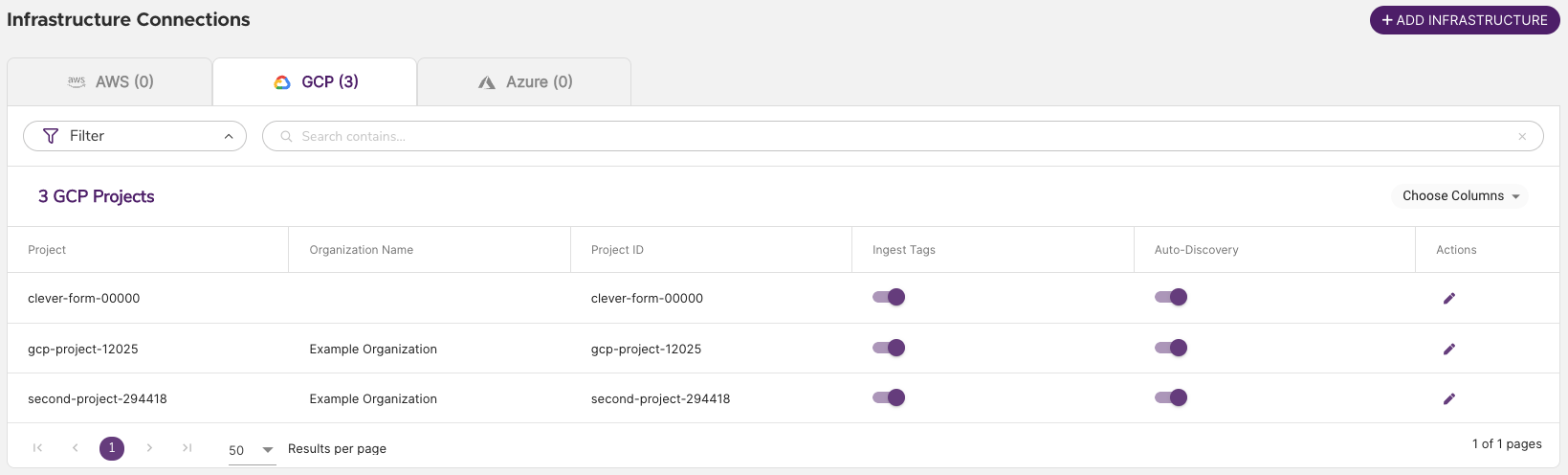
Individual GCP Project
You will repeat these steps for each individual GCP Project you wish to onboard within the Netskope One DSPM application.
Create Google Service Account
Begin by configuring a Google service account which will be dedicated to Netskope One DSPM's use.
Excerpt: GCP: Onboarding: Service Account
More information about GCP's BigQuery IAM roles is available here. Click this lin
More information about GCP's BigQuery IAM roles is available here.
- Click this link to log into your GCP IAM Console, which will navigate you to IAM & Admin > Service Accounts screen.
- Using the GCP project selector, navigate to the project for which you’d like to create the service account.
- Click the CREATE SERVICE ACCOUNT button (circled below).

- In the Service account details section, complete the following fields:
| Field | Value |
|---|---|
| Service account name | Any value; it is recommended to include "Netskope One DSPM" in the name, to make it easier to identify |
| Service account description | Any value |
- Click the CREATE AND CONTINUE button.

Click the DONE button to complete creating the service account
Add Custom IAM Roles
Netskope One DSPM Service Usage Role
Netskope One DSPM requires permission to specific Google APIs i.e. Cloud SQL Admin API,Cloud Data Catalog API and Cloud Resource Manager API to perform its scanning & discovery activities. A custom role needs to be created to automatically enable these APIs for all the projects under an organization at the time of onboarding.
Following steps need to be performed to create this custom roles
- Click this link to log into your GCP IAM Console, which will navigate you to IAM & Admin > Roles screen.
- Click the CREATE ROLE button.
- Complete the following fields:
| Field | Value |
|---|---|
| Title | Netskope One DSPM Service Usage |
| ID | CustomRoleXXX, where XXX could be any numeric |
- Click “Add Permissions” and type "Service Usage Admin" and select serviceusage.services.enable in the modal as shown below and click Add.

- To scan and classify data in Google Cloud Storage buckets, you must also add the following permissions:
- Filter permission list by Storage Admin role.
- Select the permissions shown in the image below.

storage.buckets.get
storage.buckets.getIamPolicy
storage.buckets.list
storage.buckets.listEffectiveTags
storage.buckets.listTagBindings
storage.multipartUploads.list
storage.multipartUploads.listParts
storage.objects.get
storage.objects.list- Add permissions for persistent disk discovery
.png)
compute.disks.list
compute.instances.get
compute.instances.list- Click the CREATE button to complete.
Bigquery Connection user Role
Netskope One DSPM requires a specific Bigquery custom role to be defined and applied to the service account for a seamless connection to the Bigquery data stores. Repeat the steps as above in the IAM & Admin > Roles screen to create this role.
| Field | Value |
|---|---|
| Title | Netskope One DSPM BigQuery Connection User |
| ID | CustomRoleXXX, where XXX could be any numeric |
Click “Add Permissions” and type "BigQuery Connection User" and select all the permissions in the modal as shown below and click Add followed by CREATE button to complete.

- In the Grant this service account access to project section, configure the service account's project access by granting the following GCP IAM roles:
- Netskope One DSPM Service Usage (as created in Add Custom IAM Role section)
- Netskope One DSPM BigQuery Connection User (as created in Add Custom IAM Role section)
- Cloud Spanner Viewer
- Cloud Spanner Database Reader
- Cloud SQL Admin (must be included to use Snapshot Scan with Cloud SQL data stores)
- Cloud SQL Client
- Cloud SQL Viewer
- BigQuery Data Viewer
- BigQuery Job User
- BigQuery Metadata Viewer
- BigQuery Read Session User
- BigQuery Resource Viewer
- Data Catalog Viewer
- Pub/Sub Admin (must be included to send notifications via Google Pub/Sub)
- Click the CONTINUE button.
- Click the DONE button to complete creating the service account.
Netskope One DSPM Unmanaged Discovery Role
Netskope One DSPM requires a specific custom role to be defined and applied to the service account for automatically discovering unmanaged data stores such as MySQL, PostgreSQL, MariaDB, Oracle and SQL Server, within GCP Persistent Disks. Repeat the steps as above in the IAM & Admin > Roles screen to create the role.
| Field | Value |
|---|---|
| Title | Netskope One DSPM Unmanaged Discovery Role |
| ID | CustomRoleXXX, where XXX could be any numeric |
Click “Add Permissions” and type "Netskope One DSPM Unmanaged Discovery Role" and select all the permissions listed below in the modal and click Add followed by CREATE button to complete.
compute.disks.create
compute.disks.delete
compute.disks.list
compute.disks.update
compute.disks.use
compute.disks.useReadOnly
compute.images.useReadOnly
compute.instances.attachDisk
compute.instances.create
compute.instances.delete
compute.instances.get
compute.instances.list
compute.instances.setMetadata
compute.subnetworks.use
compute.subnetworks.useExternalIp
compute.zoneOperations.getNote that the Compute Engine API must be enabled for each GCP Project for which you want to discover unmanaged data stores in GCP Persistent Disks.
Enabling this feature will result in additional costs. The total expense will vary based on the number of disks that require scanning, the duration of the scans, and the volume of data involved. These factors will determine how long the extra resources needed for scanning the disks remain active.
Generate Google Service Key
Excerpt: GCP: Onboarding: Service Key
Once the Netskope One DSPM-specific service account has been created, you can generate and download a service key, which the Netskope One DSPM platform will use for connecting with your GCP infrastructure.
- Click this link to log into your GCP IAM Console, which will navigate you to IAM & Admin.
- Within the GCP IAM Console, click on the project for which you created the above service account
- Select the service account's details by either:
- Clicking its Email hyperlink; or
- Under the Actions column, click the three-dot icon to display the sub-menu, then select Manage Details.
- Click on the KEYS tab.

- Click the ADD KEYS button.
- In the displayed dropdown list, select “Create new key”.

- On the next screen, ensure that "Key type" equals "JSON".
- Click the CREATE button to download the JSON Key File to your local machine. This file will be used in the Create a Netskope One DSPM Infrastructure Connection section below

Create Netskope One DSPM Infrastructure Connection
Excerpt: GCP: Onboarding: Infrastructure Connection 1
At this point, your configuration of GCP infrastructure is complete, and it can now be onboarded to the Netskope One DSPM application.
- Log into your Netskope One DSPM instance.
- Navigate to Administration > Infrastructure Connections.
- Select the GCP tab.
- Click the Add Infrastructure button.
- The Add Infrastructure modal is displayed.
- In the JSON Key File field, upload the JSON key you created above.
- Enter the following additional values:
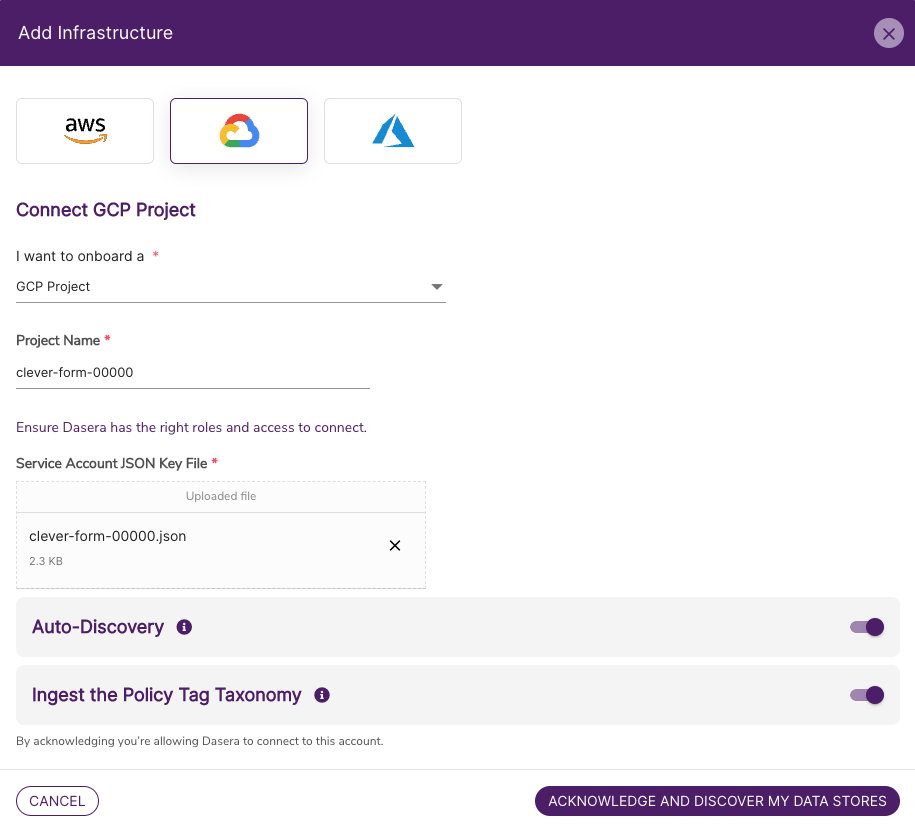
| Field | Value |
|---|---|
| I want to onboard a | GCP Project |
| Project Name | Any value (this is used to identify your Infrastructure Connection within the Netskope One DSPM UI). |
- Confirm your desired GCP Project settings (you can change your choices at anytime):
Excerpt: GCP: Onboarding: Infrastructure Connection 2
Setting Details When Enabled Auto-Discovery Netskope One DSPM will discover Data Stores with
| Setting | Details When Enabled |
|---|---|
| Auto-Discovery | Netskope One DSPM will discover Data Stores within a GCP Project. To learn more, please visit our Data Store Inventory article. |
| Ingest the Policy Tag Taxonomy | Any GCP Policy Taxonomies associated with a GCP Project will be imported. To learn more, please visit our Data Tags article. |
- Click the Acknowledge button.
At this point, we recommend that you permanently delete your local copy of the JSON Key File, to prevent any unauthorized use.
Netskope One DSPM will next verify the connection, onboard your project(s), and kick off the initial discovery of Data Stores. Once you've completed onboarding GCP Projects, the GCP Infrastructure Connections screen will resemble the following. Blank Organization Name values indicate individual GCP projects outside of any organization.
