Overview
These instructions are used for onboarding Azure Subscriptions and Tenants as Infrastructure Connections within Netskope One DSPM. Such connections permit Netskope One DSPM to discover your available Data Stores and facilitate scanning & classification activities. You will repeat these steps for each Azure Account you wish to onboard to Netskope One DSPM. In order to do that, you need to follow these steps.
Register Netskope One DSPM App Service Principal
- Login to your Azure portal and search for App registration.

- Click on New Registrations and complete the registration by providing app Name. It is recommended to include "Netskope One DSPM" in the name, to make it easier to identify.

- Go to Overview of the created app and capture Application ID and Tenant ID (Directory ID).
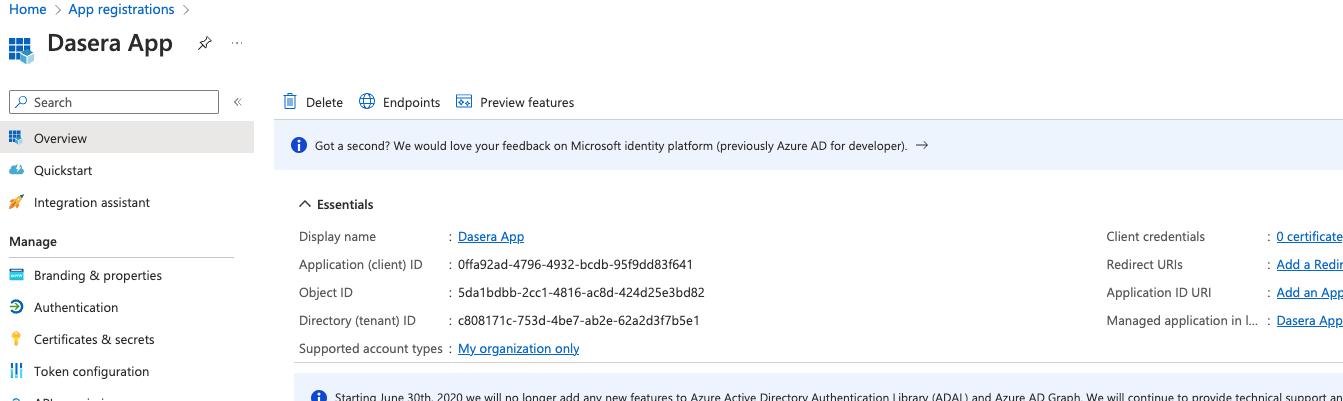
Create Client Secret
- From Netskope One DSPM App overview, navigate to Certificates & secrets and click on New client secret
- Enter Description and validity of secret
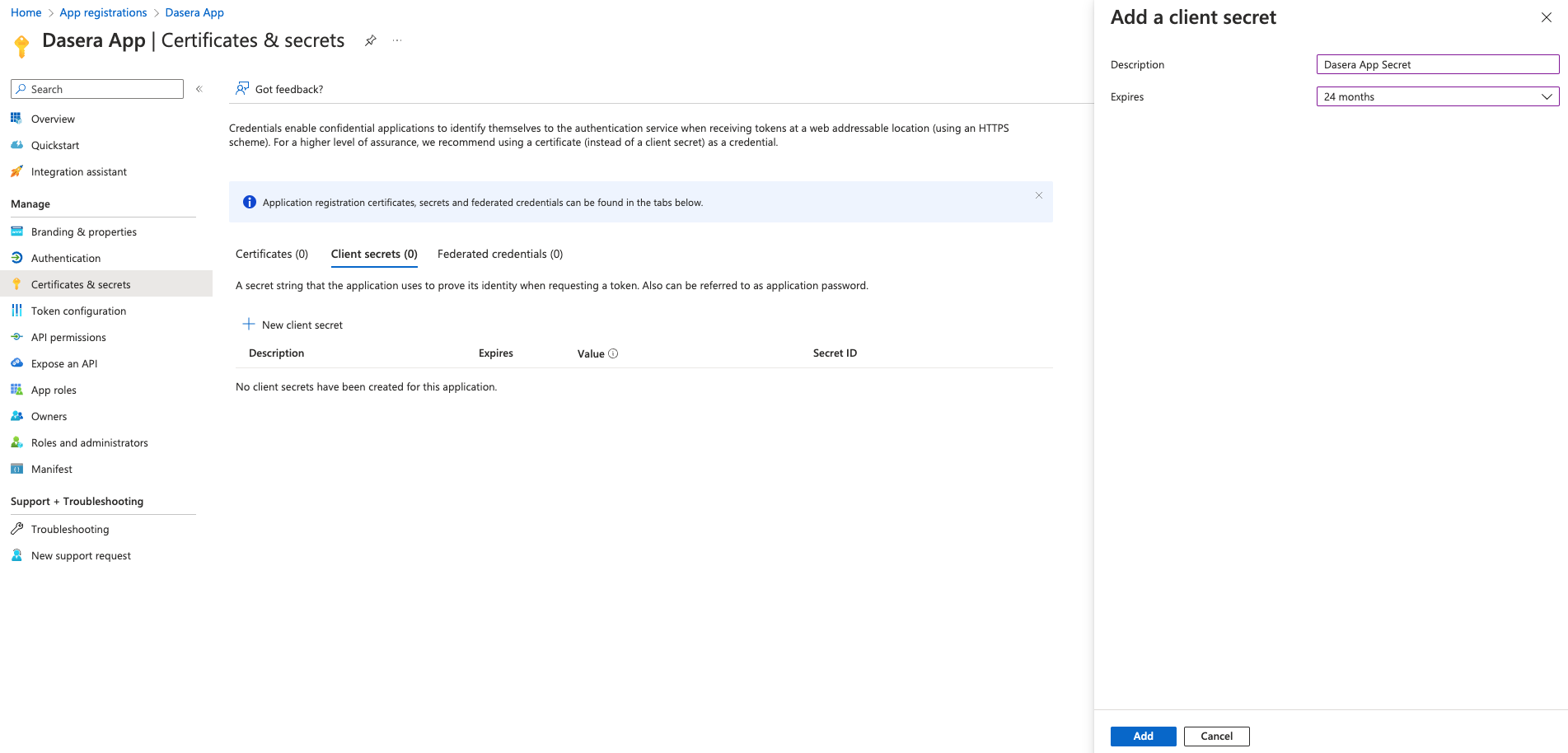
- On clicking Add the secret is created. Copy and capture the Secret value as Application Secret. The secret is never shown again after this step

Add Netskope One DSPM Role
-
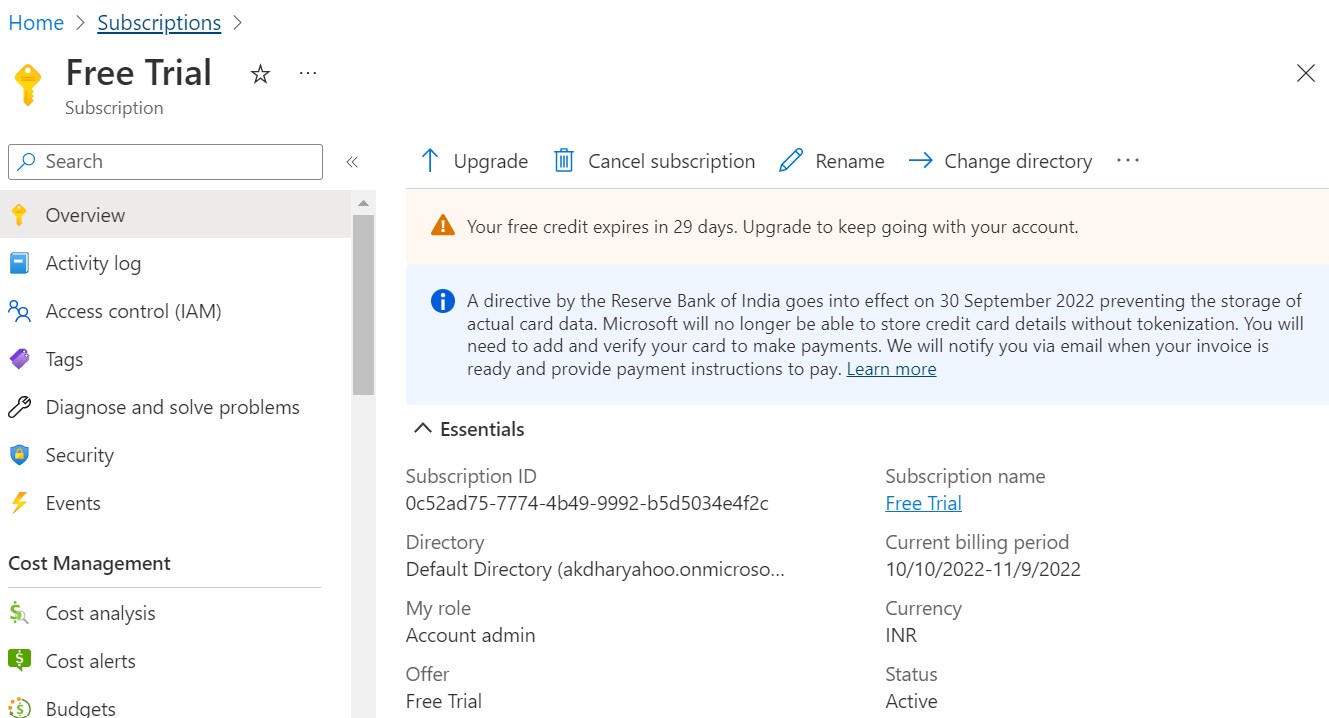
Click and navigate to Subscriptions and capture Subscription ID
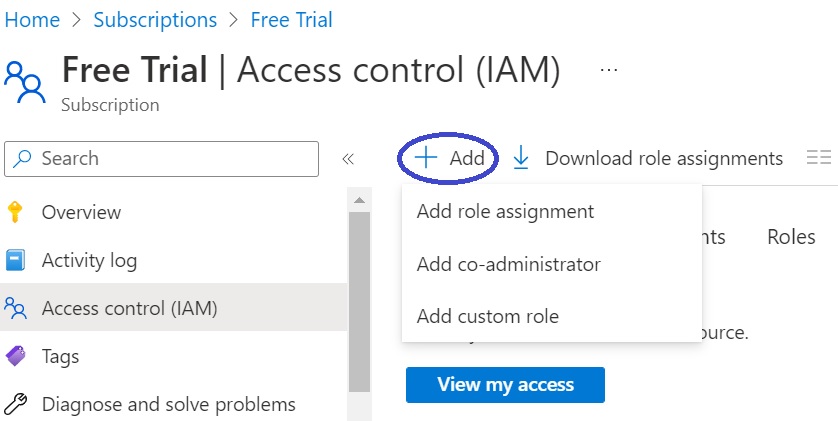
- Navigate to Access control (IAM) and Add a custom role by clicking the Add menu bar at the top
- Navigate to JSON tab and click the Edit button.
- In the text area, replace the default JSON with one of the following Netskope One DSPM-specific JSON content (expand to see the details). Be sure to substitute your Azure Subscription ID value where you see
<AZURE SUBSCRIPTION ID>.
Standard Permissions
Use this JSON for the standard permissions required by Netskope One DSPM.
{
"properties": {
"roleName": "Netskope One DSPM Role",
"description": "",
"assignableScopes": [
"/subscriptions/<AZURE SUBSCRIPTION ID>"
],
"permissions": [
{
"actions": [
"Microsoft.Sql/servers/read",
"Microsoft.DBforPostgreSQL/servers/read",
"Microsoft.DBforPostgreSQL/servers/databases/read",
"Microsoft.DBforMySQL/servers/read",
"Microsoft.DBforMariaDB/servers/databases/read",
"Microsoft.DBforMariaDB/servers/read",
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.DBforPostgreSQL/serversv2/firewallRules/read",
"Microsoft.DBforPostgreSQL/servers/firewallRules/read",
"Microsoft.DBforMariaDB/servers/firewallRules/read",
"Microsoft.DBforMySQL/servers/firewallRules/read",
"Microsoft.Sql/servers/firewallRules/read",
"Microsoft.Sql/servers/administrators/read",
"Microsoft.DBforMySQL/flexibleServers/read",
"Microsoft.DBforMySQL/flexibleServers/firewallRules/read",
"Microsoft.DBforPostgreSQL/serversv2/read",
"Microsoft.DBforPostgreSQL/flexibleServers/read",
"Microsoft.DBforPostgreSQL/flexibleServers/firewallRules/read",
"Microsoft.DBforPostgreSQL/flexibleServers/databases/read",
"Microsoft.Synapse/workspaces/read",
"Microsoft.Databricks/workspaces/read",
"Microsoft.Storage/storageAccounts/blobServices/read",
"Microsoft.Storage/storageAccounts/blobServices/containers/read",
"Microsoft.Storage/storageAccounts/read",
"Microsoft.Storage/storageAccounts/listkeys/action",
"Microsoft.Storage/storageAccounts/fileServices/shares/read"
],
"notActions": [],
"dataActions": [
"Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read",
"Microsoft.Storage/storageAccounts/fileServices/fileshares/files/read"
],
"notDataActions": []
}
]
}
}Standard + Snapshot Permissions
Use this JSON for both the standard and snapshot scanning permissions required by Netskope One DSPM.
{
"properties": {
"roleName": "Netskope One DSPM Role",
"description": "",
"assignableScopes": [
"/subscriptions/<AZURE SUBSCRIPTION ID>"
],
"permissions": [
{
"actions": [
"Microsoft.Sql/servers/write",
"Microsoft.Sql/servers/delete",
"Microsoft.Sql/servers/firewallRules/write",
"Microsoft.Sql/servers/databases/read",
"Microsoft.Sql/servers/databases/write",
"Microsoft.Sql/servers/databases/delete",
"Microsoft.Sql/servers/read",
"Microsoft.DBforPostgreSQL/servers/read",
"Microsoft.DBforPostgreSQL/servers/databases/read",
"Microsoft.DBforMySQL/servers/read",
"Microsoft.DBforMariaDB/servers/databases/read",
"Microsoft.DBforMariaDB/servers/read",
"Microsoft.Resources/subscriptions/resourceGroups/read",
"Microsoft.DBforPostgreSQL/serversv2/firewallRules/read",
"Microsoft.DBforPostgreSQL/servers/firewallRules/read",
"Microsoft.DBforMariaDB/servers/firewallRules/read",
"Microsoft.DBforMySQL/servers/firewallRules/read",
"Microsoft.Sql/servers/firewallRules/read",
"Microsoft.Sql/servers/administrators/read",
"Microsoft.DBforMySQL/flexibleServers/read",
"Microsoft.DBforMySQL/flexibleServers/firewallRules/read",
"Microsoft.DBforPostgreSQL/serversv2/read",
"Microsoft.DBforPostgreSQL/flexibleServers/read",
"Microsoft.DBforPostgreSQL/flexibleServers/firewallRules/read",
"Microsoft.DBforPostgreSQL/flexibleServers/databases/read",
"Microsoft.Synapse/workspaces/read",
"Microsoft.Databricks/workspaces/read",
"Microsoft.Storage/storageAccounts/blobServices/read",
"Microsoft.Storage/storageAccounts/blobServices/containers/read",
"Microsoft.Storage/storageAccounts/read",
"Microsoft.Storage/storageAccounts/listkeys/action",
"Microsoft.Storage/storageAccounts/fileServices/shares/read"
],
"notActions": [],
"dataActions": [
"Microsoft.Storage/storageAccounts/blobServices/containers/blobs/read",
"Microsoft.Storage/storageAccounts/fileServices/fileshares/files/read"
],
"notDataActions": []
}
]
}
}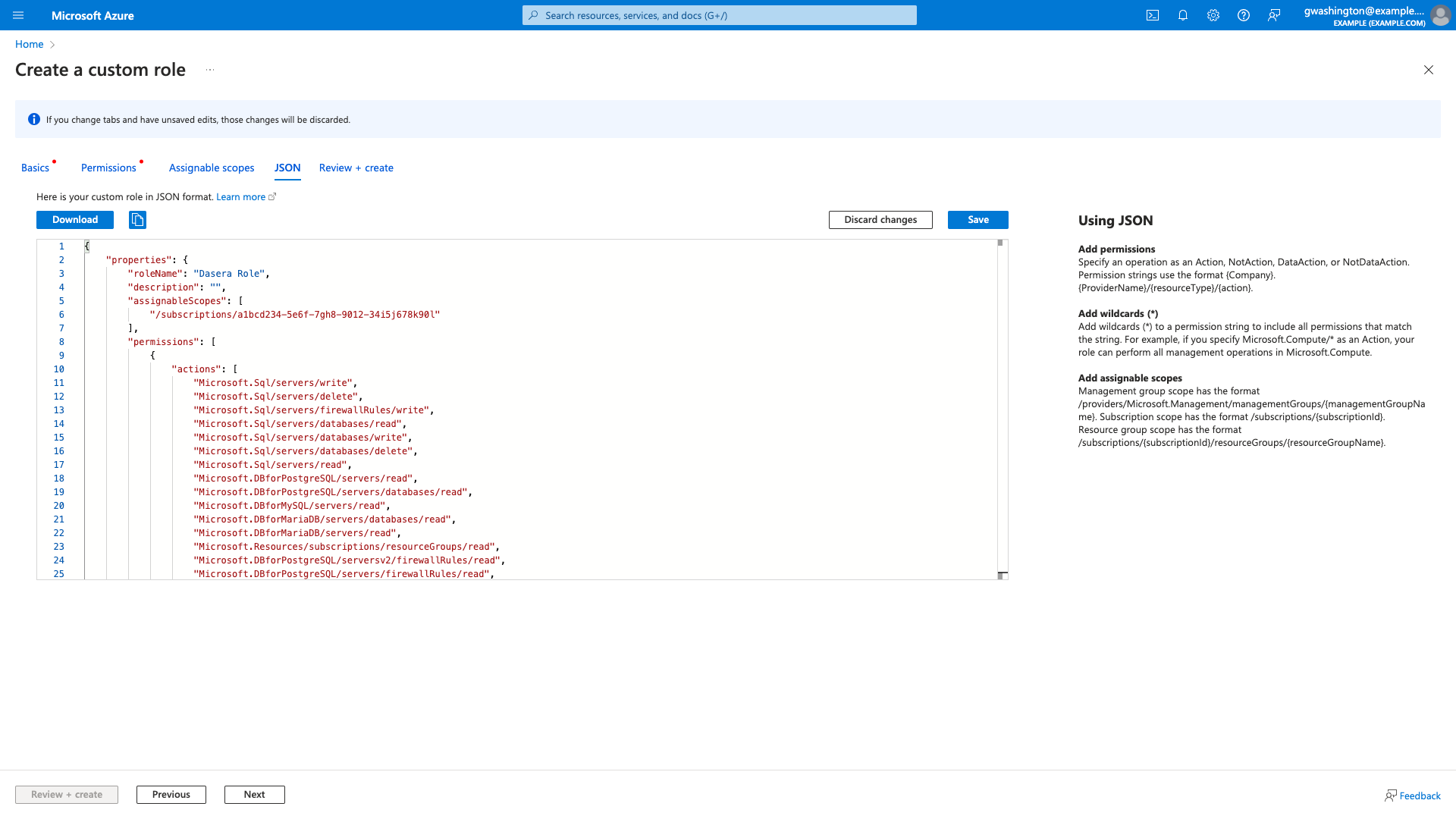
- Click the Save button.
- Click the Review + Create button. The review screen is displayed.
- Click the Create button.
Assign Role to Netskope One DSPM App
Add Netskope One DSPM RoleClick on Review and Create and Click OK button to complete creation of required custom role.
Next, we have to assign this custom role to our app. For this click on Add role assignment
- On the Roles tab, filter for the role created for Netskope One DSPM and click the Next button.
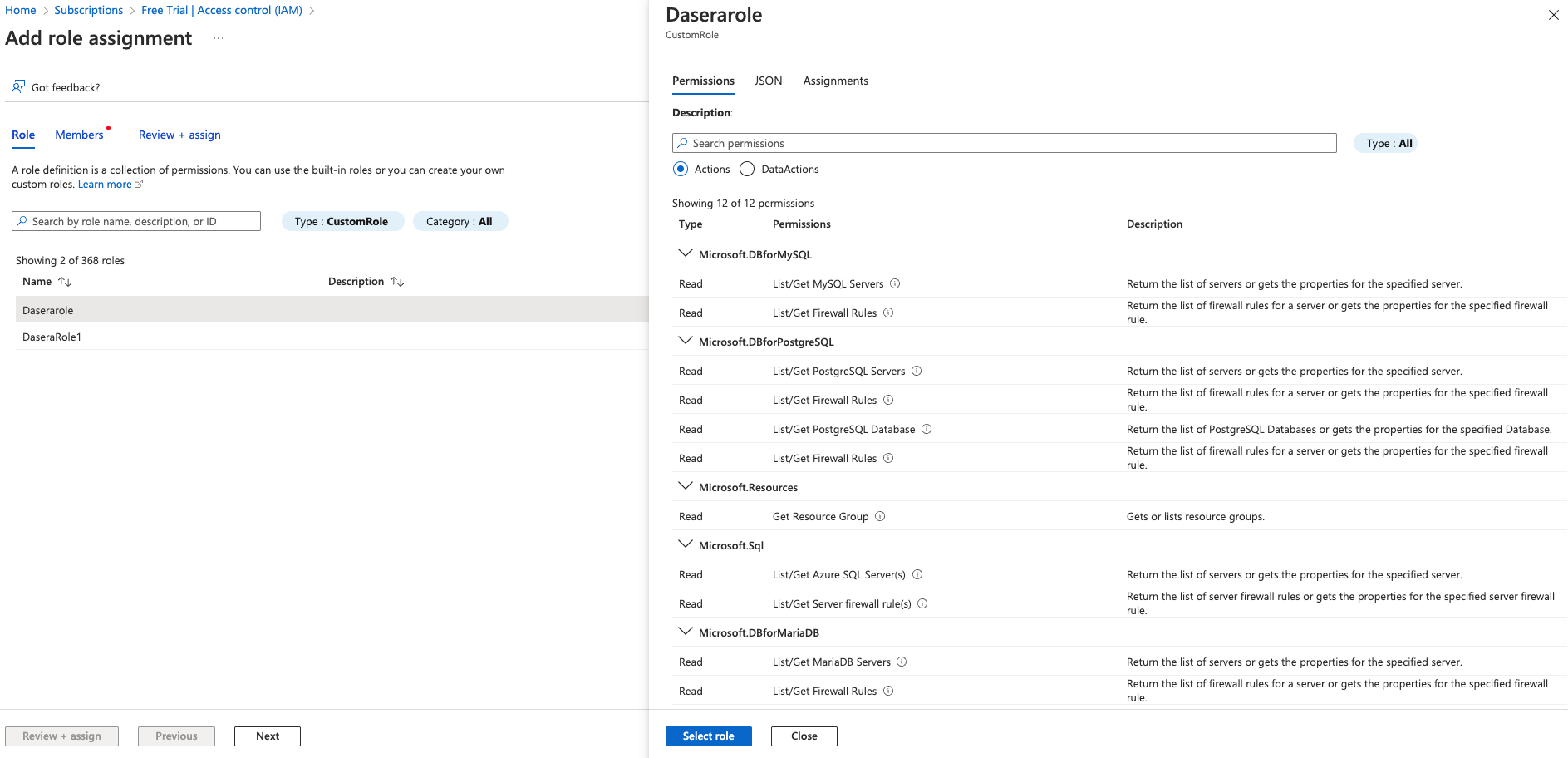
- On the Members tab:
- Click the Select members button
- In the drawer that displays, filter for the application created for Netskope One DSPM
- Select the application and click the Select button
- The drawer will auto-dismiss
- Click the Next button
- On the Review + assign tab, click Review + Assign to complete the role assignment
Grant permissions for automatic misconfiguration analysis (Optional)
- Click and navigate to App registrations, select Netskope One DSPM App and navigate to API permissions
- Click on Microsoft Graph (1) and click checkbox for permission Application > Application.Read.All and Update permissions
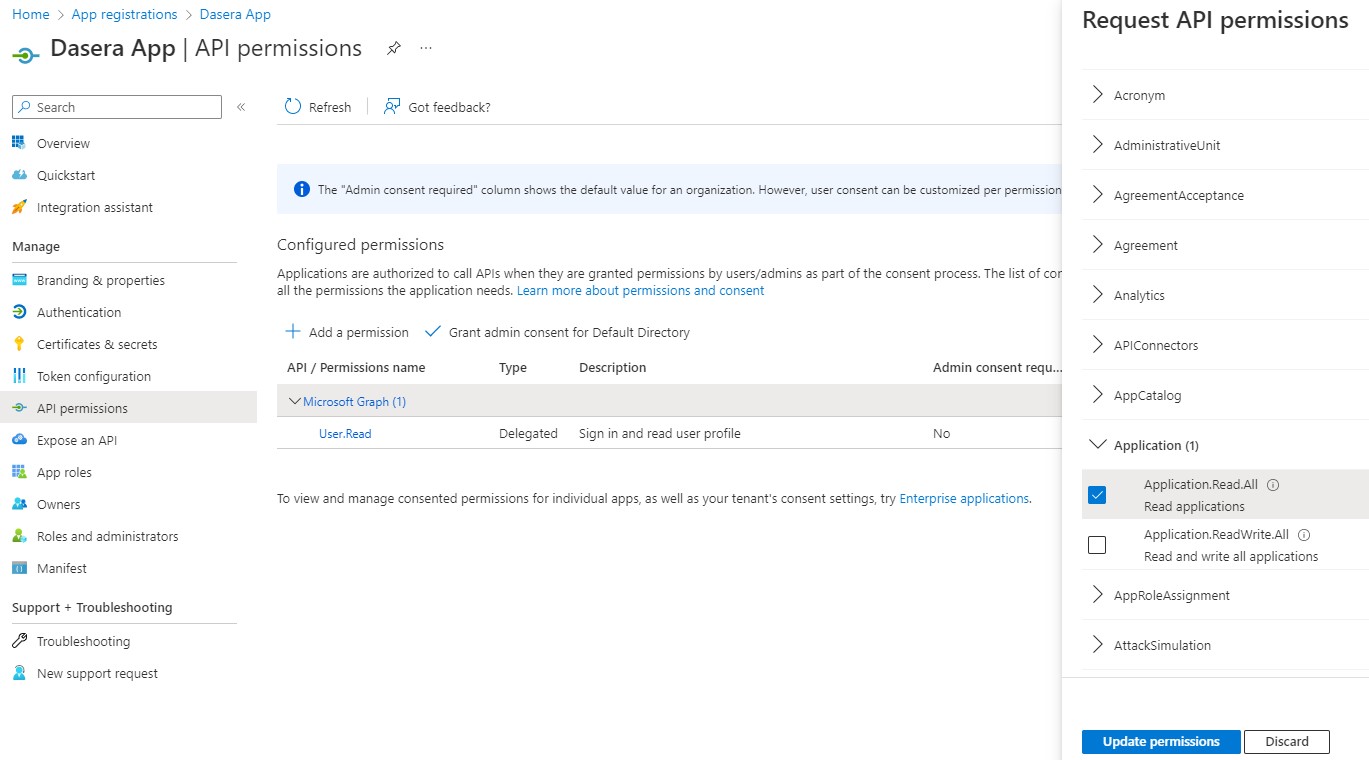
- Once above permission is added, Grant admin consent to remove the warning icon.
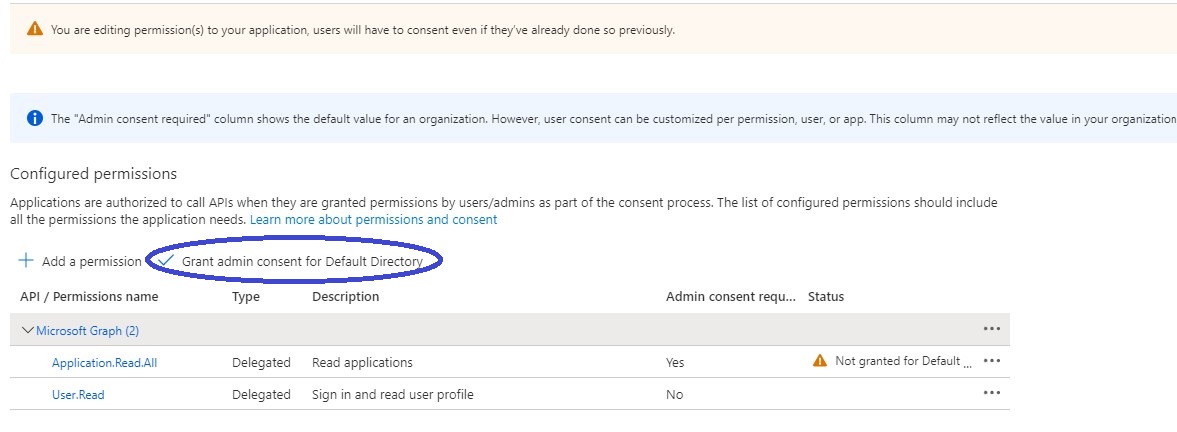
Grant permissions for unmanaged data store discovery (Optional)
- Click and navigate to App registrations, select Netskope One DSPM App and navigate to API permissions
- Add permissions Azure Service Management : user_impersonation, Azure Storage : user_impersonation, Microsoft Graph :Group.Read.All, Microsoft Graph :Group.Read.All, Microsoft Graph :User.Read.All
.png)
- Once above permission is added, Grant admin consent to remove the warning icon.
Note on Azure VM Quota Requirements
During deployment, customers may encounter an error related to exceeding the Azure standardESv3Family core quota (e.g., OperationNotAllowed). This feature requires larger VM sizes, which may exceed the default quota in certain regions (e.g., East US). To resolve this, customers should request a quota increase through the Azure Portal.
For more information on monitoring and managing quotas, refer to Azure Quota Monitoring and Alerting.
Create Netskope One DSPM Infrastructure Connection
- Log into Netskope One DSPM
- Navigate to the Administration > Infrastructure Connections screen > Azure tab
- Click the Add Infrastructure button
- Enter the following values:
| Field | Value |
|---|---|
| Account Name | Any value (this is used to identify your infrastructure connection within the Netskope One DSPM UI). |
| Tenant ID | Enter the Tenant ID captured in point 3 in Register Netskope One DSPM App Service Principal section above |
| Application ID | Enter the Application ID captured in point 3 in Register Netskope One DSPM App Service Principal section above |
| Application Secret | Enter the Application Secret (value) captured in point 3 in Create Client Secret section above |
| Subscription ID | Enter the Subscription ID captured in point 1 in Add Netskope One DSPM Role section above |
- Click the Acknowledge button
Next Steps
- If you have additional Azure Accounts to onboard in Netskope One DSPM, repeat the above steps.
- Connect your discovered Data Stores. For more information, visit our Connecting Azure Data Stores category and select the article(s) applicable to the Data Store Type(s) you wish to connect.