Major New Features
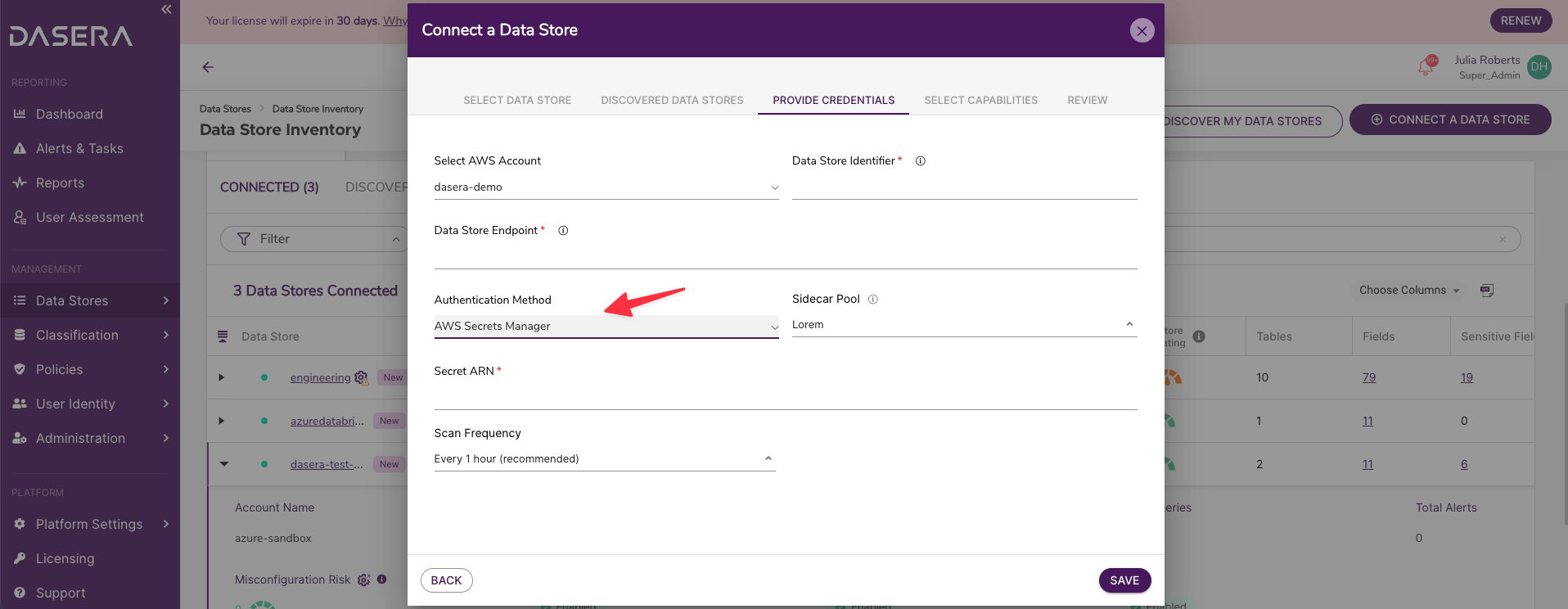
Secrets Manager support for Data Store Credentials
AWS Secrets Manager
Netskope One DSPM now supports using AWS Secrets Manager to authenticate and connect to most AWS Data Stores, eliminating the need to store your Service Account credentials within your Netskope One DSPM SaaS instance. Learn more about using AWS Secrets Manager.
Self-Managed Secrets Manager
Netskope One DSPM also now supports using Self-Managed Secrets Manager (such as Vault or Kubernetes Secrets Manager) to authenticate and connect to most Data Stores, eliminating the need to store your Service Account credentials within your Netskope One DSPM SaaS instance. Learn more about using Self-Managed Secrets Manager.
Support for Azure Databricks
Netskope One DSPM now allows you to connect to your Databricks data stores within your Azure cloud infrastructure. Once connected, Netskope One DSPM automatically performs Discovery and Classification of all data within the data store, helping you drive and optimize your Data Lifecycle Security Strategy. Learn more about connecting to Azure Databricks.
SSO User Management via Identity Provider
You can now use your SAML-compatible Identity Provider (including Okta Universal Directory and Azure Active Directory) to provision Netskope One DSPM users with specific platform roles. When users log into Netskope One DSPM via SSO, their platform roles will be dynamically assigned. Learn more about SSO User Management.
Improvements and Updates
Filter by Last Scan Status
From the Data Store Inventory screen (Data Stores → Data Store Inventory), you can now filter by Last Scan Status, quickly seeing which of your data stores may be experiencing network issues.
New Misconfiguration Policy Updates
Misconfiguration Risk in your Data Stores now appears as specific risk scores, corresponding with low, medium, high, or critical risk ranges from the Configuration Analysis page. When creating a Policy for Misconfiguration Risk, you can create policy conditions that trigger Alerts based on specific Risk scores exhibited by your Data Stores.
