Connecting with AWS Aurora MySQL Data Stores
Overview Netskope One DSPM supports scanning AWS MySQL Data Stores. Follow these instruction
Overview
Netskope One DSPM supports scanning AWS MySQL Data Stores. Follow these instructions to setup your MySQL database and configure its connection to Netskope One DSPM.
These instructions are for connecting an individual MySQL Data Store. To learn more about onboarding many MySQL Data Stores at once, please visit our Connecting to multiple MySQL Data Stores article.
Authenticate Data Store
There are two methods for authenticating RDS and Aurora data stores: Snapshots or Service Account.
Using Snapshots
Snapshots are quicker and simpler, spinning up a secure copy of the data store for Netskope One DSPM to scan without needing to create a Service Account. This copy exists only within your Netskope One DSPM instance, and Netskope One DSPM does not store any associated data. It's encrypted and then immediately spun down, so there are no lingering data copies. Please note that spinning up the data store copy can cause the scan initiation process can take several hours.
The following features are not supported when authenticating via Snapshot:
- Privilege Analysis
- Data-in-use monitoring
- Database selection
- Sample data collection
Ensure you've enabled data store Snapshots access during AWS Infrastructure onboarding. For already onboarded accounts, you must manually add permission AmazonRDSFullAccess in the AWS Console.
Once connected, data classification in the data store runs via Snapshot, which appears on the Data Store Inventory page as a small layered square note icon to the right of the hyperlinked data store name. You can later edit the data store and turn off Snapshots, at which point a Service Account will be required to authenticate the data store.
Using a Netskope One DSPM Service Account
Begin by configuring a MySQL service account which will be dedicated to Netskope One DSPM’s use. The following instructions apply to all of the cloud infrastructure solutions listed above. Authentication to RDS is supported using either password- or IAM-based authentication.
The following steps may require the assistance of your AWS and/or local database administrator.
IAM-based authentication
Configure RDS
- As an administrator, log into your AWS RDS Console.
- Navigate to the database you wish to connect
- Under the Configuration tab,
- Within the Summary section, make note of the Region value
- Within the Instance section, ensure that the IAM Connectivity setting is enabled

- As an administrator, log into your MySQL database's shell using these AWS instructions.
- Create the Netskope One DSPM-specific MySQL user by executing the following commands in order:
| Command | Outcome | Notes |
|---|---|---|
|
Creates the Netskope One DSPM-specific user for authentication using the AWS RDS plugin. |
Substitute
|
|
Grants to the Netskope One DSPM-specific user the required permissions which power capabilities within the Netskope One DSPM platform. |
Substitute
|
Configure IAM
- As an administrator, log into your IAM Dashboard.
- In the left-hand menu, select the Roles menu item.
- Using the search box, find and open the Netskope-specific role.
- Most likely, it is named “Netskope_Role” if it was created using the CloudFormation template or Terraform script provided by Netskope
- Otherwise, you are welcome to create a new custom role and ensure it has the same Trust Relationship as the Netskope-specific rule.

- The role summary screen is displayed.
- Under the Permissions tab, click the Add Permissions button
- In the dropdown, select the Create inline policy option.
- On the Specify Permissions screen, click the JSON button.
- In the Policy editor section, overwrite the default JSON with the following, replacing the following values:
| Placeholder | Value |
|---|---|
[REGION] |
The AWS region where your RDS database resides, as identified in the Configure RDS step above |
[ACCOUNT] |
Your AWS account number |
[USER] |
Your DB user, as defined in the Configure RDS step above |
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"rds-db:connect"
],
"Resource": [
"arn:aws:rds-db:[REGION]:[ACCOUNT]:dbuser:*/[USER]"
]
}
]
}If your plan to connect with RDS databases in more than one AWS region, add additional rows to Resource object, one for each region you will eventually connect with.
When complete, your screen should resemble the following:

- Click the Next button.
- On the Policy Details screen, enter the following values:
| Field | Value |
|---|---|
| Policy Name | Any value. It is recommended to use “Netskope_Policy_RMS", so it is clear the purpose of this custom addition to the Netskope-specific role |
- Click the Create policy button.
When complete, your final Netskope-specific role definition should resemble the following:

Password-based authentication
- As an administrator, log into your MySQL database's shell using these AWS instructions.
- Create the Netskope One DSPM-specific MySQL user by executing the following commands in order:
| Command | Outcome | Notes |
|---|---|---|
|
Creates the Netskope One DSPM-specific user for authentication using a password. |
Substitute
|
|
Grants to the Netskope One DSPM-specific user the required permissions which power capabilities within the Netskope One DSPM platform. |
Substitute
|
Configure Query Logging (Optional)
Netskope One DSPM’s Data-In-Use-Monitoring capability requires access to query logging. If you wish to leverage this capability, you must configure your MySQL instance to begin generating such logs.
Users who have the MySQL permission to set the sql_log_off session variable can disable logging for their own session (and the separate permission to set set restricted session variables). For optimal security and audibility, the ability to access & adjust this setting should be restricted.
Excerpt: MySQL Query Logging Performance Impacts
Enabling query logging on a MySQL database may impact its performance. Once you have completed these configurations, closely monitor your database along with any pipelines / applications that are dependent on it.
These changes will require a MySQL server restart to take effect. It is recommended you schedule this reboot during an internally-publicized maintenance window in order to least impact your users.
The following steps may require the assistance of your local database administrator.
Please follow the steps below to define these configurations:
- Click this link to log into your AWS RDS Console, which will navigate you to the RDS service.
- Under Amazon RDS in the left-hand menu, navigate to Parameter groups.
- Select an existing parameter group for your MySQL database. If one does not exist, create a new one using these AWS instructions.
- On the next screen, click the Edit parameters button.
- Using the search box, find the following parameter keys and set the corresponding values:
| Flag | Value |
|---|---|
| general_log | On |
| log_output | TABLE |
- Click the SAVE button.
- As an administrator, log into your MySQL database's shell using these AWS instructions.
- Continue your logging setup by executing the following command:
| Command | Outcome | Notes |
|---|---|---|
|
|
mysql.rds_rotate_general.log is a function delivered with all AWS MySQL databases. For more information, please visit the AWS RDS documentation. To limit the size of logs, AWS RDS will call this function whenever logs exceed 10GB or 10% of database space. You can also configure your MySQL server to call this function on a regular cadence (ex: every week, monthly, etc). |
- Restart your MySQL server at your earliest convenience.
Retrieve Connection Information
In addition to configuring a service account, Netskope One DSPM will also require additional information in order to communicate with your MySQL instance. Please follow the steps below to identify the connection values for later use within Netskope One DSPM.
- Click this link to log into your AWS RDS Console, which will navigate you to the RDS service.
- Under Amazon RDS in the left-hand menu, navigate to Databases.
- For the database you wish Netskope One DSPM to scan, click its link in the DB Identifier column. For Aurora MySQL, be sure to choose a database with Role = "Writer Instance" (instead of "Regional cluster")
- In the Connectivity & security section, make note of the following values:
| Highlight Color | Corresponding Netskope One DSPM Value | Example |
|---|---|---|
| Blue (Endpoint) | Data Store Endpoint |  |
| Grey (Port) | Data Store Endpoint | 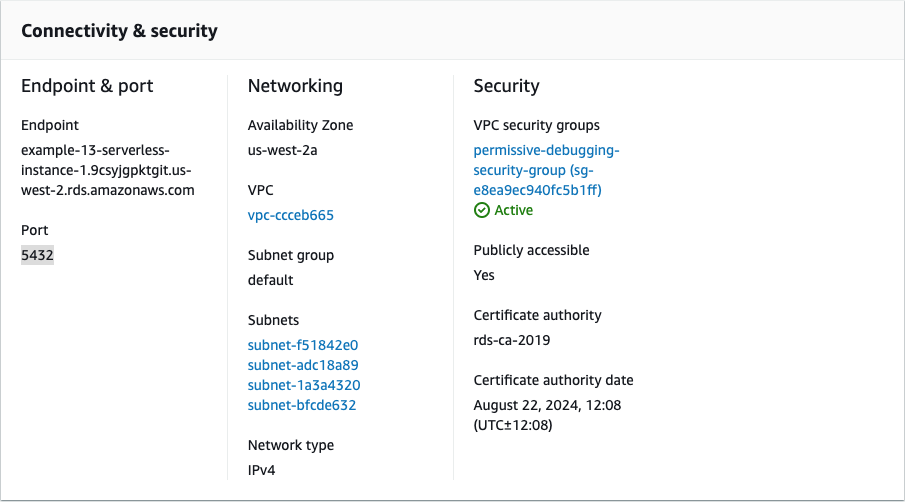 |
Connect Your Data Store
Before attempting to connect a AWS Data Store, be sure you have configured a Netskope One DSPM-specific AWS Service Account and onboarded the AWS Infrastructure for this Data Store.
Excerpt: Connect Your Data Store 1
Log into the Netskope One DSPM platform. Navigate to the Data Stores > Data Store Invento
- Log into the Netskope One DSPM platform.
- Navigate to Data Stores → Data Store Inventory.
- Use the Discovered tab, then click the CONNECT button under Actions to connect a discovered data store. You'll immediately see the Credentials tab with some fields automatically populated.
- Alternately, click the CONNECT A DATA STORE button in the upper right to select a data store type and go through the data store connection UI manually.

- The Connect a Data Store modal is displayed, starting with the SELECT DATA STORE tab.
- Click on the icon for the Data Store Type you wish to connect. The modal will auto-navigate you to the next tab.
- On the PROVIDE CREDENTIALS tab, complete the following fields:
| Field | Value |
|---|---|
| Select AWS Account | Select one of the AWS Accounts defined within the Infrastructure Section screen. The field will default if there is just one AWS Account configured |
| Data Store Identifier | Provide a friendly name to describe this Data Store. Your value is displayed in other Netskope One DSPM screens such as Policy Management and Classification Management. |
| Data Store Endpoint |
Enter the corresponding values from the Retrieve Connection Information step above, plus the port number. For example, for an address like 3306 is the default MySQL port number. If you are using a custom port number, be sure to substitute it here. |
| Authentication Method | Select the desired authentication method |
| Database Username | Enter the corresponding value from the Using a Netskope One DSPM Service Account step above. |
| Password | When Authentication Method equals “Username / Password”, enter the corresponding value from the Using a Netskope One DSPM Service Account > Password-based authentication step above. |
| Scan Frequency | Controls how often your Data Store is reviewed for changes, Netskope One DSPM’s recommended frequency is defaulted, which you can override if desired. |
| Sidecar Pool | Excerpt: Connect Your Data Store: Credentials: Sidecar PoolIf you will use sidecars to monitor this data store, select a sidecar pool with network visibility to said data store. This field is displayed when there is at least one defined sidecar pool. To learn more, please visit our Sidecar Administration article. |
Excerpt: Connect Your Data Store 2
Click the NEXT button, which will navigate you to the next tab. On the SELECT CAP
- Click the NEXT button. The SELECT CAPABILITIES tab is displayed.
- Complete the following fields:
- Assign a Data Owner (optional): define one or more Platform Users responsible for this Data Store and its data sets.
- Which databases should Netskope One DSPM scan?: utilize the field’s picklist control to select which databases & schemas should be monitored by the Netskope One DSPM application. By default, all databases & schemas are selected.
- Features: Netskope One DSPM’s recommended feature selections will be defaulted, which you can override if desired. Some features are always-on, some are not applicable (with disabled toggles), while others may request additional configurations.
| Capability | Supported for AWS Aurora MySQL via Service Account | Supported for AWS Aurora MySQL via Snapshots |
|---|---|---|
| Discovery | Yes (always-on) | Yes |
| Privilege Analysis |
Yes MySQL version 8.0 or higher is required for this capability. If you are using an older MySQL version, disable this setting before continuing. |
No |
| Shadow Data Analysis | Yes | No |
| Classification | Yes | Yes |
| Data In Use Monitoring |
Yes Query logging must be configured for this before enabling this capability. See the Configure Query Logging section above. |
No |
| Automation | Yes (always-on) | Yes |
Excerpt: Connect Your Data Store 3
Click the NEXT button, which will navigate you to the next tab. On the REVIEW tab
- Click the SAVE button, which will navigate you to the next tab.
- On the REVIEW tab, Netskope One DSPM will validate your credentials and capability selections. In the event of any issues, follow the on-screen instructions to remediate the displayed warnings or errors.
- Click the SAVE button to finalize your connection.
If you encounter the error “Unable to access system logs for MySQL database”, be sure to double-check your logging configurations in the Configure Query Logging section above.